Featured Articles
Use a Password Manager Tool
The main reason you want a password manager is so that you don't have to remember your passwords except for the one to access the...
Read More "Use a Password Manager Tool"
Maintain Unique & Complex passwords
Risks of compromised passwords Where does that password go once you establish it? It must reside somewhere in order to compare what you entered and...
Read More "Maintain Unique & Complex passwords"
Staying Secure
Hidden Risks of Browser Plugins
Why You Should Avoid Browser Plugins to Protect Your Privacy Browser plugins...
Read More "Hidden Risks of Browser Plugins"
Privacy – Disable Autofill
Just because you did not type personal data on a website does...
Read More "Privacy – Disable Autofill"
Choose Search Engine Privacy over Quality
It’s really an amazing story on how Google became a verb. Yet,...
Read More "Choose Search Engine Privacy over Quality"
Control the Trackers
Companies are not putting up websites, loaded with news, information, or other...
Read More "Control the Trackers"
Utilize a UPS Device
An Uninterrupted Power Supply (UPS) is essential equipment for: Desktop Computers Network...
Read More "Utilize a UPS Device"
Use Multiple e-mail Accounts
Electronic mail (aka: e-mail or email) is a necessary evil for communications....
Read More "Use Multiple e-mail Accounts"
Install OS and App updates ASAP
These updates aren’t necessarily to make your use of the application better....
Read More "Install OS and App updates ASAP"
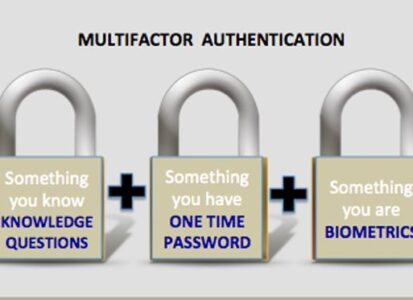
Use Two-Factor Authentication
If a website has 2FA or MFA available to you, then USE...
Read More "Use Two-Factor Authentication"
Obfuscate names viewable by the public
Cellphone: Do not name your Hot Spot after you or otherwise personalize...
Read More "Obfuscate names viewable by the public"
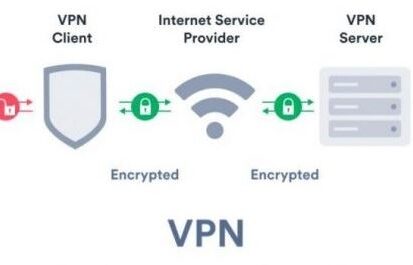
Know when to use VPN
VPN means “Virtual Private Network”. It’s akin to having your own private...
Read More "Know when to use VPN"
Connecting to Wi-Fi Networks
You do not need Wi-Fi so badly that it’s worth risking all...
Read More "Connecting to Wi-Fi Networks"
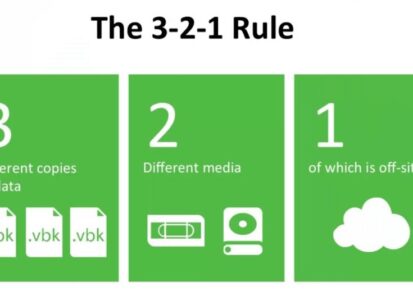
3-2-1 Backup Strategy
Overview of backup strategy You need a backup strategy to protect the...
Read More "3-2-1 Backup Strategy"