Risks of compromised passwords
Where does that password go once you establish it? It must reside somewhere in order to compare what you entered and what the website (or a 4th party) has stored. Some companies use partner authenticator parties like Google and Facebook. If they say it’s okay, then the site depends on the authetication partners authorization to allow you access. Alternatively, most often in addition to, the websites house login credentials themselves. Regardless of method, the actual password (or a hash of the password as computed via an algorithm) is stored in a data field within in a data table residing in a database housed on disk(s) within a volume located on a Server in what is likely a Data Center. But that’s an educated guess. The fact is that you do not know how the password is stored at every website and the methods for storage vary greatly. It’s not like a standard exists for how to store usernames and passwords that every company followed. Rather, we (in the Information Technology industry) learned over time and developed best practices over time This presents a lot of risks, none of which you personally have control:
- Passwords, especially from the 90’s, were often stored in clear text. This means anyone with access to the database can read the password.
- Passwords may have been encrypted, but the token to decode the encryption may be easily obtained by employees
- Encryption may have been in use, but its implementation is poor such as poorly managed keys
- Companies may have gone bankrupt and were unable to invest in proper data destruction techniques
- Old data backups or archives may have fallen into the wrong hands
- Active, good standing, companies may have holes in their defenses, allowing bad actors to gain access to user credentials
- Background checks are good predictors of future behavior, but not 100% infallible. Employee(s) having privledged accounts might use it as a criminal opportunity.
Passwords must be unique. Why unique?
For the reasons I just described, you cannot trust the companies are able to protect your password. So, if they can’t protect it, you must use a different one for every single website.
It’s common for individuals to have over a hundred website accounts. It’s a given that some websites are weaker than others. If they have a breach, YOU have a problem if your passwords are the same across sites.
The best protection is a unique password; meaning, a different password for every single website you have an account with. This assures you that a breach does not put you at risk across the web! It makes selling the data to nefarious actors unproductive since the password is/was only good at one location. If the company identifies the breach and expires your password immediately, it does nothing to safeguard that same password if used on other websites.
Password must be complex. Why complex?
Complex Passwords? Yes, very complex passwords are needed. Passwords that you can’t easily socially engineer. Common passwords like 123456, password, qwerty, password123, and so on are effectively no password at all. As an example, let’s look at banking websites. Many banks allow you to use your account number as the user ID. That’s a bad idea, but it’s happening… especially at smaller ones like Credit Unions. Account numbers may be issued sequentially. So, let’s imagine you use a simple password… let’s go with aa12345678 (this is the 14th most common password used). All the hacker needs to do is populate the account number sequentially and then try the same aa12345678 password for each one. If just 1% of the accounts used this common password, and the Bank has 10,000 customers, then they were successfully able to breach 100 accounts. That’s a simple case that someone without hacking skills might use to effectively hack their way in.
Computer algorithms are publicly available to help hackers. They can plug a formula into the algorithm such as password length is 8 and look for alphabetic upper case and lowercase. Because there are just 26 alphabetic characters, multiplied by 2 for case sensitivity, the combinations are limited… allowing a computer to auto attempt a password pretty quickly (I mean seconds, not hours).
This table demonstrates the power of using long and complex passwords:
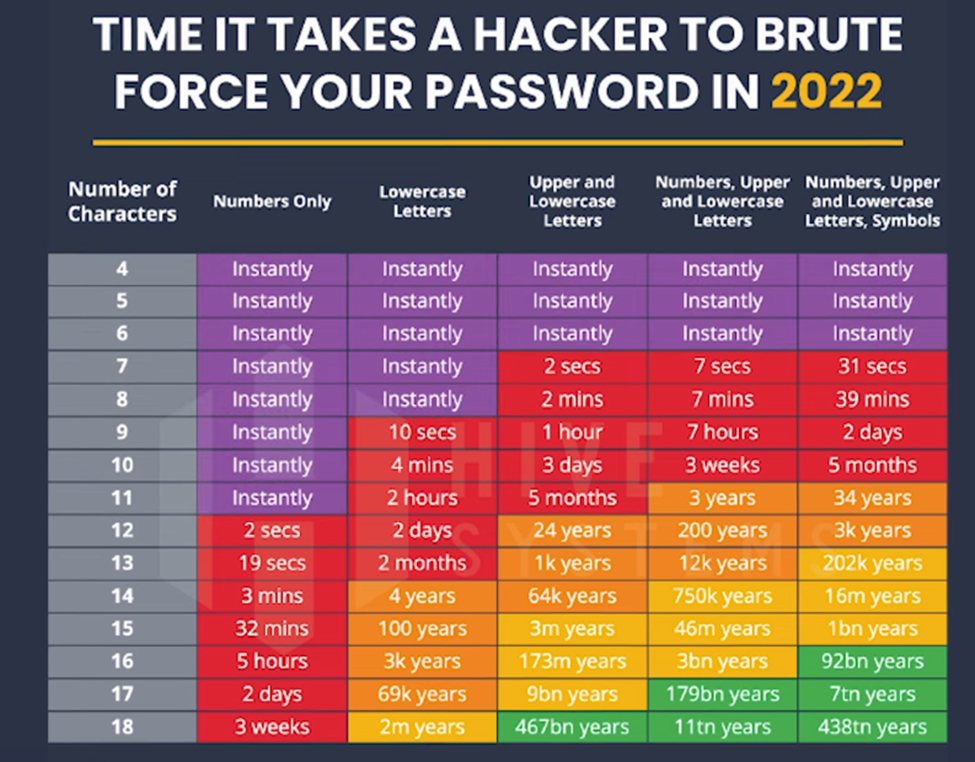
I strongly suggest, urge you to use a minimum of 14-character passwords with a mix of Upper Case, Lower Case, numbers, and special characters.
A few examples to talk through:
A sweet but weak password – 1LoveMySpouse
A fantastically strong password – 14Tt!/irk7#3215rps+3xYR6p
A memorable but still strong password - Pepper-9-NewYork-8-forecast-7-goats-6-coworkers&indiansWhy is the first example weak? After all, it does have 13 characters. And it’s using Alphanumeric. It is weak because it’s using words from the dictionary that logically go together as one would use in a sentence. Hacker search engines use words from the dictionary, and their numeric substitution equivalence (e.g. using a 0 in place of O so Love is now L0ve, 3 in place of E, and 1 in place of L or I); so effectively the 1LoveMySpouse password has a strength of only 4 dictionary words. If you’re going to use dictionary words, there should be at least 6 of them and they should not logically combine. This password can be cracked in less than a second.
Why the second password is strong should be self-evident: Due to the length (25-characters), lack of words from the dictionary, and variety of character sets used, this is an extremely complex password to crack.
Why the last example is also strong is because of its length and use of numbers, Mixed Case characters, and symbols. This type of password is good if you need to memorize it. But, because you should not have the same password across websites, and the likelihood of memorizing hundreds of word phrases is low, use of this method is limited. Note that this password uses 6 random words, and then sprinkles in numbers and special characters.
You’re thinking… oh common… nobody, and I mean absolutely nobody, can remember that strong of a password. And, if they are different for every site, that’s an impossible ask! You’re right! But the password is not for your convenience, it is to keep others out. And the others we speak of are normally being helped by computers with superpowers.
If you only take one piece of this advice, it adds little value to your protection. You need to do both parts (unique and complex). Why?
81% of data breaches are due to poor passwords. This is, by far, the tip I’m begging you to implement above all others.
Don’t fret – I have some suggestions and tools to help.

