Imagine you live in a house on a street alongside many other houses. And outside your house you see hundreds of suspicious people walking up and down the street, lurking in windows, walking up to doors to test if it’ll open, and walking up to every window to test if it can be opened. They carry notebooks and write down when you and your neighbors leave, what you leave with, and when and what you come back with. Sounds absolutely horrible! You’d probably move.
Your computer, your smartphone, and all other internet connected devices are subject to this scenario. Nefarious actors are testing your devices hundreds of times a day and log what they find out.
Blogs on this site originated as a result of friends and family reaching out to me as a result of internet scams or hacks, and because I’m skilled in this area. Blog entries here are intended to help you protect yourself from the threats on the Internet.
Who am I to provide tips?
It is an intentional act that my name is absent:
- I have zero aspirations to becoming a public figure, preferring to maintain my privacy.
- All the advice discussed in the blogs is intended to protect your privacy. I, too, desire to protect my privacy.
My profession of over 3 decades in the Information Technology field puts me in a unique position that provides significant visibility into Internet threats, and what corporations are doing to protect themselves. My responsibilities include working with Global Information Security officers in Fortune 500 companies to identify threats and remediate computer applications to protect corporate systems and their data in our care from nefarious actors.
Additionally, I work with Assessment Firms which use hacking tools to identify weaknesses so that we can remediate them before a breach occurs. There are dozens of companies I work with whose job it is to find weaknesses in websites. This is where “White Hat” hackers gain employment to do what they love legally with full disclosure and without then exploiting the weaknesses. White Hat is a name given to Hackers that use their skills for good. Corporations hire the companies to identify their weaknesses. The Assessment Firms create detailed reports identifying weaknesses so the Corporations can remediate the problems. Then, the Assessment Firms retest the weaknesses to see if the remediation worked.
Some Corporations invest heavily in security measures to keep your data safe (and their reputation). Some corporations learn the hard way where a huge security breach has changed their policies, causing them to invest more heavily in data security. And, then there are most corporations, especially smaller ones… or mom & pop shops… that aren’t even close to understanding the threats and dealing with them.
Based on public information, it would be very difficult to pick and choose the corporations you do business with based on how well they protect data. But what you do have control over is YOU. You can do actions with the devices you use that will help protect you.
The Zeltar Consulting goal
My goal is to provide tips that help you protect YOU. We all know locking your house and car helps defend them from theft. And, that what someone can see through the windows can be enticing, so we obstruct the view of high value assets from the windows. Computers (this includes cell phones, and smart devices like DVR’s and the latest appliances) are a lot harder to protect. And it’s harder to detect if someone’s breached your computer than it is your car or house.
Like the image I painted in my opening, we’d probably freak out if our home’s front door lock was tested just once. If it was tested every single day, we’d probably move! Your computers defenses are tested FAR MORE than you would imagine.
How bad is it?
Your computers, without your knowledge (unless you have specialized tools), are fending off thousands of attacks a week. Not a few. Not hundreds. But quite literally thousands of attempts! To illustrate, the below chart is the Intrusions detected on a home network during a 6-hour window. To catch these threats, the tool is using about 35,000 intrusion protection rules as provided by Suricata which is powered by definitions from Emerging Threats (a company which exists to know and identify threats).
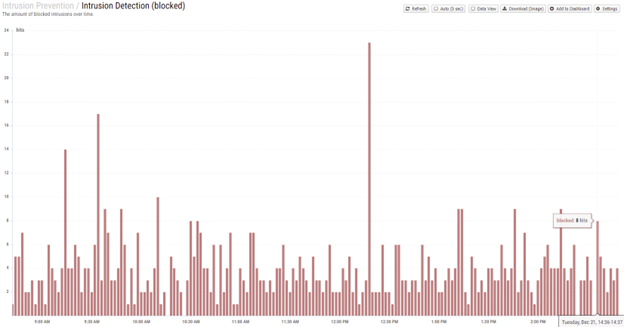
Total intrusion detection is averaging 266 attempts per hour. The tool allows one to drill down into any single attack or probe attempt and expose details of the attempted intrusion. This is not the focus of this site, as it is too much for most audiences. Rather, the intent of the sample graph is to show the activity networks must defend against. Bad actors attempting to probe household connections to the Internet to identify if a vulnerability exists. If found, that hole is captured and then exploited later to worm their way into the residential local in-home Wi-Fi network. From the weakest device attached to the network, they can launch an attack on the most valuable devices.
As most people do not have such tools to see this and the background in technologies to have any fluency in dealing with these treats, the blogging here is meant to advise you on how to stay safe.
Some of these blog entries will be the same as what you should be hearing from media sources. What I’ll do is break it down to why it’s important and try to provide strategies to make using the tips plausible and practical for the average residential user. Other blog entries will address Data Protection, especially against both hackers and companies profiting from profiles they build about you which are based on your internet activity.
Why should this have importance to you?
Your computer typically has information on it that’s a goldmine to thieves or it has enough data to provide a path to websites that contain such information. That might include:
- Your retirement savings (e.g., IRA and 401(k) accounts, Social Security)
- Your Personal Identifying Information (i.e., Data that can be used to steal your Identity)
- Your financial wellbeing – Banking, Credit Cards, and possibly tax information
Additional to the financial harm that can be inflicted upon you by any breach above, entry onto your devices allows for:
- Ransomware – to encrypt all your data files and then ask for a Ransom to grant you the privilege of accessing your own data. Paying the ransom is not a guarantee they’ll release the data or that they won’t re-encrypt your data at a later date and hold it for ransom again.
- Use of your computer to launch an attack on other computers (hiding their Identify behind yours – making you look like the criminal)
- Installing malware or a virus. Most often these days, the preference is to install trackers to monitor and gain information (such as user ids and passwords).
Hopefully, through a series of blog entries, I can help you protect you.

