If a website has 2FA or MFA available to you, then USE it.
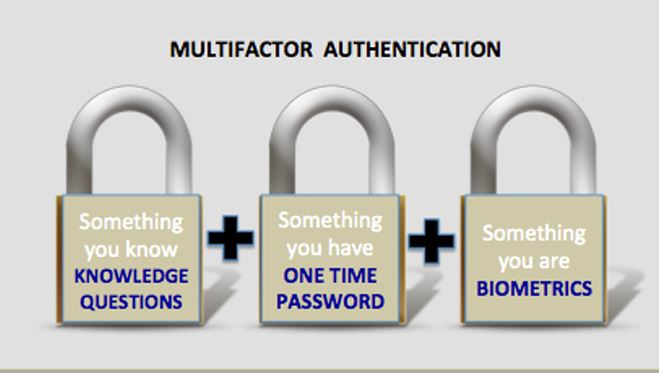
- 2FA = Two-Factor Authentication
- MFA = Multifactor Authentication
MFA and 2FA are used interchangeably in this blog.
Other terms used in this blog entry:
- TOTP = Time-based One-Time Password
- OATH = Open Authentication (an industry-wide collaboration to develop an open reference architecture using open standards to promote the adoption of strong authentication). It is NOT related to OAuth (Open Authorization), a standard for access delegation.
- SMS = Short Messaging Service is a text messaging service typically used on cell phones
And, if given a choice as to how you want to implement 2FA, then use the first option below if possible. If not, then work your way down the list:
- Hardware token
- YubiKey by Yubico
- Other OATH Hardware Token providers sushc as DeepNet Security, RSA, and Token2
- Use a TOTP software authenticator tool. The mobile phone app store contains a couple of good options:
- Microsoft Authenticator
- Google Authenticator
- Use a Phone Call or SMS Text Message
- Email – Have an email sent to you with the PIN
Before I dive deeper into why you want to use two-factor authentication, let me preface with a rule you must follow when using these. Never, Ever, regardless of who is asking, inform someone else what the code sent to you is. Nefarious actors have pretended to be the websites support and had you repeat the code to them so they can “help” you. These codes are ONLY for you to access the website yourself, not for someone on the other end of a text or phone to do it for you.
I’m going to give you an exception to the rule, which really pains me to do. The very people that should help protect you, banks, violate the rules of MFA security. Actually, many banks outsource this service to Early Warning Services, LLC. Either way, if you have used MFA, you know the text message having the PIN also usually informs you not to share the texted PIN. But, sadly, in the event fraud is detected, and the bank (or Early Warning) calls you to inform you of the breach, they first want to verify they are talking to YOU. And, to do this, they’ll text a code just like MFA does. And they’ll want you to tell them that code. If you want control of your account again, you’ll need to comply with their demand. With persistence, and if you have a landline available and within reach at the time of the incident, they may bend their rules and call you at the landline to verify you pick up. WARNING – Scammers know how the fraud department works validation, so they’ll pretend to be the fraud department to get you to send them the PIN so they can access your money. As a result, your best of the bad options is to hang up and call the bank at the number you know to be true (i.e. the number on the back of the Card or the number on the statement). If possible, it’s also a good idea to just login to your bank site directly because if fraud was detected, it should say so immediately upon login.
Please review this Better Business Bureau article on this topic:
https://www.bbb.org/article/scams/18596-scam-alert-hit-delete-on-phony-banking-texts
The priority order is significant.
- Hardware Tokens are the most secure multifactor authentication methods available and is far superior to TOTP software authentication tools below. If unauthorized access to data would be disastereous to your life, then you need to secure it with a hardware token.
- TOTP authentcator applications are far superior to the SMS and email options below. It is more secure because a code is generated on your device rather than being sent across the network, where it might be intercepted. However, there have been reports of hackers stealing authentication codes from Andriod smartphones. They do this be trycking the user into installing malware that copies and sends the codes to the hackers.
- SMS, also known as text messaging, is the most common method used. The code is sent to your cellphone. There are several hacks used to undermine this 2FA method. The most common being SIM swapping (e.g. tricking service provider that they are you and a victim so need a replacement SIM) and message mirroring.
- Your email – This is when the PIN is emailed to you. The PIN is usually valid for 15 to 30 minutes. The email protocol, known as SMTP (Simple Mail Transfer Protocol) was created in early days before security was a concern. Data in SMTP Protocol is sent without any encryption. The information can be captured while in-transit. And, most email systems also do not encrypt the emails at-rest (while sitting at your email providers site). Free email providers make their money off your data, which includes content of your email. If your email provider is encrypting email, than this option is about equal to the security of the SMS option.
Why use two-factor authentication?
Simply put, it’s an extra layer of security. If someone gets ahold of your password and 2FA is enabled, then that password is of no use. For websites with 2FA enabled, when you’re accessing from an unknown device (or the known device has been timed out), then it requires you to provide a PIN number (typically 5 or 6 digits) within a short amount of time (typically under 20 minutes).
Let’s use an example. Let’s say you opened an email or webpage that contained a hidden piece of HTML that installed a keyboard logger on your laptop. Of course, you would not know this happened and it could have happened months ago. Imagine this piece of code identifies when you click on a password field on any webpage, and then automatically captures the keystrokes and sends them to the nefarious actor. Sadly, this scenario is not far-fetched. Invisible keyboard loggers are available on the web. If you enabled 2FA, then the nefarious actor is stuck. They don’t have your separate device that receives the 2FA Pin. If aggressive, they move to phase 2 and try and get you to give them the PIN… which is why I prefaced with the rule. Don’t give out the PIN.
What is it like to use 2FA?
Each website has its own way to enable 2FA. Once enabled, the way it functions depends on which authentication method you selected.
Let’s use Amazon and a TOTP authenticator app as a Use Case. Amazon allows for 3rd party authentication tools like Microsoft Authenticator. When you set it up, they send a QR code (which is that square box your camera can read which brings up a website). This QR code provides seed information to your local app which provides data informing it how to calculate the code based on the date and time.
To use this as a login… you login to Amazon the same way you always do… you type in your Username and password. Or you can let your Password Manager tool do this for you. If Amazon determines that
- You are accessing the site from a new device associated with the user credentials provided
- You have accessed setup configuration
- You remain logged in, but you have navigated to an elevated secure page
… Amazon will display a window asking you for the 2FA PIN.
To get the requested PIN you open your Authenticator App on your smartphone. This might require your face or fingerprint to open. Amazon should be listed as one of the apps. A PIN number will be displayed. A timer, or circle that is acting like a timer, will identify how much time before that PIN expires. PINs expire every 30 seconds. You’ll want to type in the PIN number on the webpage BEFORE the PIN expires in the Authenticator App. If there isn’t enough time to enter the PIN, wait for the PIN to change giving you a new 30 second period of time to work with.
Why use a hardware token?
This seems hard, often has a cost to obtaining, and its something not to lose. This is true! It should be thought of much like an ATM card. To access your bank account at an ATM, you need more than just the PIN. You need something physical. The hardware token is that physical device. Unlike your cellphone, it’s not connected to the internet (i.e. essentially, airgapped to protect it from malware). When plugged into a USB port, or via NFC, it’s able to use a hash message authentication code exchange to authenticate you much like your browser negotiates a secure HTTPS SSL 1.3 communications channel between your browser and a secured website. Note that this is NOT using some simplified 6 digit code. This is using long encryption keys.
Not all sites take hardware tokens. The two places you should focus on with this level of security are:
- Financial Institutions: If your financial institution has these available, then they may want to send you their own hardware token such an RSA token. They might even charge a small fee. This is worth doing, especially for investment accounts that may contain funds meant to carry you through retirement. Thi s is your money! You should do everything you can to make sure it stays yours.
- Email account(s): Some email providers also allow for hardware tokens such as Yubikey. Think about all the communications sent to your email. This tells a hacker a lot about you and helps then phish and use that information to impersonate you (e.g. calling your financial institution and convincing them that they are you). As a result, you shoul use a hardware token to secure email.
Why use a TOTP authenticator application?
Far more websites allow use of an authenticator tool than the hardware token, so this is the security level everyone should acquaint themselves with. You usually carry your cellphone, so this method would be readily available. Authenticator Tools are a secure way to protect the PIN. The amount of time the PIN is active is so short the nefarious actors have to pressure you (their target) in real time to make their crime work. Nefarious actors also can’t send fake text (SMS) messages to trick the user into giving them the PIN.
The SMS Text message experience
Most websites that have 2FA aren’t sophisticated enough to use an Authenticator Tool. Or they have identified it’s not worth the investment, so they don’t invest. SMS Texting is the most common method to receive a PIN from 2FA.
When you registered, again maybe for Amazon 2FA, you set it up so your cellphone receives a text message. When you login to the site and the PIN number is needed, Amazon will send an SMS Text message to your phone. You type in the PIN number texted to you.
SMS texting is considered a weak 2FA method because text messaging, while the message is in-transit, is unencrypted. This makes it viewable to hackers having such skills. Additionally, SMS hijacking can be done with messaging mirroring applications. If you have become their target and the nefarious actor knows your mobile number, they can get the 2FA codes just like you. They would still need your user name and password though, so if those have not been compromised, you’re still okay.
Using email for 2FA
Using email can be frustrating sometimes because it might not show up in a timely fashion. Or it could land in a junk folder. Most of the time, this method works to get the PIN. Using this method is FAR better than not using two-factor authentication at all. BUT I will write a future blog entry on what’s wrong with email in general which will enlighten you on the vulnerabilities with this method. Security officers recommend the other options over email
Getting Started
Like the password manager tool, start slowly. Not all websites have this ability. Most people have an Amazon account, and their mechanism is a pretty good way to get your feet wet. After Amazon, move on to social media. Facebook can be setup with 2FA and is one of the most common apps people try and hack. Check to see if your financial institutions support 2FA. If they do, activate it!
This one from Thio is rather old (he’s gotten older and wiser now); but all his points are still valid.
Theo